
Telecommunications
English
Prerequisites
Deterministic and Random Signals
Markov Chains Theory
Queueing Theory
Information theory
Resources
Foundations
Introduction
What is the Telecommunication?
It’s the transmission of information by a communication medium using signals such as wires, radio, and optical. So, its mission is to transmit a bigger amount of data in the least time at a distance, with quality and safest.
Is “Information and Communications Technology (IT)” a bad name?
Delivery.
Accuracy
Timeliness.
Jitter.
Networks
A network is a set of nodes interconnected by a medium (link) to transfer data. More concretely in telecommunications, a network is a combination of hardware and software that sends data from source to destination.
hosts (end systems)
Graph theory
Telecommunication and network relationship
The telecommunication goal is to communicate nodes in a network.
Performance.
Reliability.
Security
Why are telecommunications and networks important?
They are so important because humanity needs communication, the fastest communication possible. Today, we generate data they have to deliver instantly for different motives such as business, news, government, health, and entertainment. Internet, radio, television, and other mediums are cheaper than at other times, so they generate opportunities with the biggest impact and a little money. For instance, social networks like Facebook and Twitter are impossible with no telecommunication infrastructure.
Computers and Internet have changed our learning way, YouTube offers free top-tier university courses such as MIT OpenCourseWare, Stanford, Harvard, and other greatest professors in different topics.
During the COVID-19 Pandemic, the world didn’t stop because humanity has connected since XX. Remote work emerged as a solution for thousands of jobs, and school from home was possible thanks to telecommunications, videotelephony software systems, and the Internet.
For previous reasons, telecommunication and the Internet allow humanity lives better.
General communication model
Text
Numbers
Images
Audio
Video
Time
Epoch
Round-trip delay
Data communications
It transports information from A to B by a medium with signals. Cifrado.
BPS (bit per second), k, M, G1
Checksum
CRC-32
SHA-256
Multimedia, MPEG
Protocols and Standards
Protocols and standards are two crucial concepts that allow communication. On one hand, “protocol” means a set of rules governing the transmission of data between nodes. In another hand, “standards” are protocols and other kinds of specifications established by a large consensus.
Since the data is language, protocols refer to the specifications that the language, timing, and metadata (headers), but note that protocols and standards don't say anything about implementation.
Language specifications refer to the lexical, syntax, and semantics specifications. Timing refers to the speed of the data and the date to send them. Metadata (headers or control information) is data that provides data about the payload such as the payload’s size, payload source, payload destination, authorization, and authentication.
Protocolos son las reglas que usamos en el alfabeto (análisis sintáctico) para dar significado (análisis semántico) para ello necesitamos una carga útil o mensaje + Información de control (encabezados -headers- o metadata que ayudan a procesar o recibir el mensaje).
Authors give different dimensions to study standards: by the property (open, closed), by the way to consensus (de facto, de jure).
De facto standards are ones that have not been approved by an official organization.
De jure standards are an official organization's recommendations. Some are not mandatory, it depends on the government, for instance, NOM in Mexico.
An open (free/libre) standard is one that is openly accessible by anyone. The standard is kept secret by an organization if want to use it you have to use a special product.
Some organizations that make standards are ISO, IEC, IEEE, ANSI, ITU, RFC (IETF), RFC editor, W3C, and manufacturers consortium.
| Example | |
| De facto and open standard | Web |
| De facto and closed standard | MS Word |
| No standard protocol | An example is your API REST Resources which communicates the service to the client. |
| De jure and open standard | HTTP https://datatracker.ietf.org/doc/html/rfc9110 |
| De jure and closed standard |
In this book, we’re going to study the different protocols following the OSI standard. Indeed, mastering this field is equivalent to learning fully protocols.

References
Welcome | acm sigcomm. (2022, November 04). Retrieved from https://www.sigcomm.org
https://www.csun.edu/senate/resolutions/Open Standards Resolution.pdf
https://wiki.p2pfoundation.net/Main_Page
https://www.ibm.com/blogs/cloud-computing/2019/04/02/open-standards-vs-open-source-explanation/
Lie, H. (2005). Opera to MS: Get real about interoperability, Mr Gates. The Register. Retrieved from https://www.theregister.com/2005/02/11/hakon_on_ms_interroperability
https://en.wikipedia.org/wiki/Open_standard#ITU-T_definition
Home. (2022, November 22). Retrieved from https://www.ietf.org
Index of /rfc. (2022, November 15). Retrieved from https://www.ietf.org/rfc
[Sta04] and [PD03].
[Tan03]
Interconnection model
An interconnection or suite has to be specified in order for nodes to communicate with each other. Since a protocol is not enough to make a built communication channel successfully, we need an interconnection model or protocols suite based on system design principles to manage system complexity. Some of them are:
- Hierarchy. The model defines layers and their “precedence order” to execute them.
- Service. Each layer has services to the layer immediately above it.
- Encapsulation. Each packet (data and metadata) at layer is encapsulated in the packet at level .
- Interfaces Between Layers. Layers communicate with adjacent layers with well-defined interfaces.
- Organization. The system is divided into layers.

The OSI Model
Once upon a time when the interconnection model was dominated by the OSI model, today TCP/IP suite became dominant thanks to the Internet. We discuss the OSI model briefly given its importance.
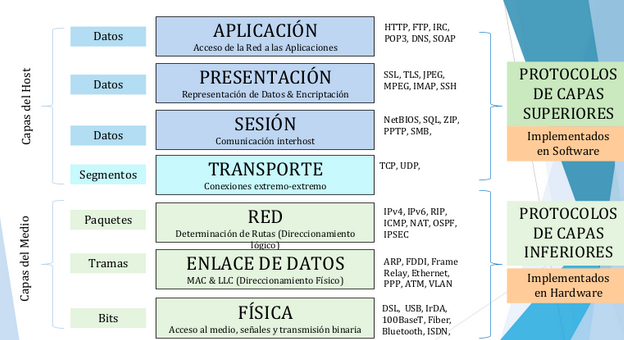
TCP/IP Protocol suite
Ecosystem
MDL mllab.com
ITAR-Registe
https://www.corning.com/cala/es.html
Jobs
Exercises Set
Story
1700-1800 Electricity, electromagnetic, and mathematics
Fourier, Laplace, and Cauchy make mathematics Tractatus.
Hans Christian Oersted and Andre-Marie Ampere do electricity and magnetic experiments.
Micheal Faraday and Joseph Henry discovered electromagnetic induction.
George Simeon Ohm discovered Ohm Law.
Alessandro Volta discovered battery principles.
Electricity (Breakpoint)
Electromagnetism
Maxwell, Hertz, Lodge
Guglielmo Marconi
Nikola Tesla
1800-1900 Telegraph, phone, and radio
Carl Gauss and Wilhelm Weber developed the first telegraph.
William F. Cooke and Charles Wheatstone started the first telegraph company and a patent for its telegraph in the UK. Charles proved music that can transmit by wires too.
Samuel Finley Breese Morse invented the electric telegraph and communication code called Morse code in the US.
Antonio Santi Giuseppe Meucci invented the first mechanical phone, but he don’t patent it. Alexander Graham Bell was the first to patent it.
James Clerk Maxwell does the electromechanical theory.
Heinrich Rudolf Hertz extends Maxwell’s electromechanical theory.
Guglielmo Marconi was the first to the patent radio, but Tesla invented it.
1900-1950 Television, satellites, and computers
Paul Nipkow invented Nipkow disk.
John Logie Baird extended the Nipkow disk.
Charles F. Jenkins did the first experimental TV transmissions.
Vladimir Zworykin invented a TV Communication system employing cathode ray tubes.
John Von Neumann and al. invented EDVAC, the first general electric computer.
AT&T in Bell laboratories invented the transistor by William Shockley, Jonh Bardeen, and Walter Brattain.
Clark proposed the satellite concept.
Hady Lamarr
Radio
AM, FM
DARS
SW
Sirius XM
Space
Clark
Satellites
NASA
Telstar I
INTELSAT, Early Bird
Pay Per View
ANIK
HBO
Ted Turner (WTBS)
TNT
CNN
Superstation
Mexico Morelos I, Morelos II, Solidaridad I, Satemex 5 https://mapasatelital.ift.org.mx
Television
Phone Cellular
In world
Phone Cellular was born in Japon
In Mexico
1990 MX (Telcel, Telefonica, Unefon, …) ?
Locatel?
DTH
Internet
https://www.submarinecablemap.com/
Generation in mobile
1G FDMA
2G GSM, CDMA, TDMA
3G UTMS, WCDMA
4G
5G
Sobre el cancer.
FAQ
Sources of Digital Information
Physical Layer
Signals
A is Amplitude
f is the frequency (hertz)
It’s fase
Oscilloscope
g(t)
g(f)
spectrum analyzer
Fast Fourier Transform: time → frequency
Waveform
Square
Rectangular
Sinusoidal
Digital signals
Analog signals
Digital Signals = f(EMI, Analog Signals)
Analog signals = f(EMI, Digital Signals)
Wavelength
AM Signal 300 m
FM Signal 3 m
Analog phone 0.33 m
Digital phone 0.17 m
Attenuation.
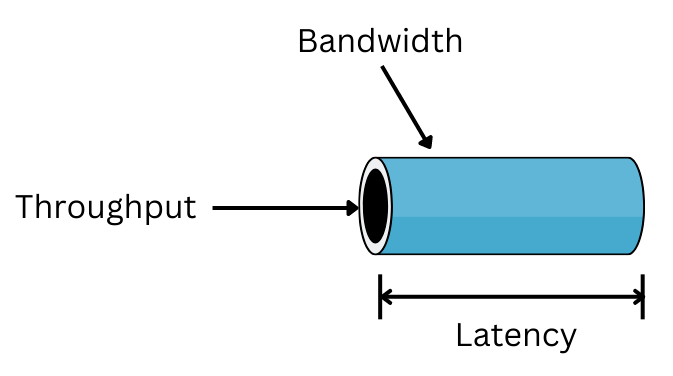
Bandwidth
Bandwidth is the maximum number of bits that flows on a connection in a period of time. The fundamental unit of network bandwidth is bits per second (bps). It also means the range of frequencies used to transmit signals.
- Variable.
Bits per rate (bps).
- Fixed.
Analogous Mode.
FM can transmit data, but AM not.
FM, AM are analogous information.
He was assigned by the government.
X-Ray
Tomografias
Waves and signals.
Ripper??
Throughput
Throughput is the actual number of bits that flows on a connection in a period of time. So, by definition, .
Latency
How works the signal?
Beacon.
What is an antenna?
The antenna is a filter.
Electromechanic.
VHF
UHF
Antenna and wavelength relationship.
Frequencies
VLF
LF
MF
HF
VHF
UHF
SHF
SHF
EHF
IR
Visible light
WalkieTalkies
ISM?
RFID
Homework
Optical fiber
Shannon–Hartley theorem
Nyquist theorem
Analog-digital conversion
Discrete and continuous signals.
Analog and digital.
Signal.
Sampling.
Codification.
Analogous database??
Regeneration??
Digital transmission?
Extended Spread Spectrum
Noise-Signal relationship
Why do humans prefer digital over analog signals?
Dolby Digital
Ripping

Telecommunications Mediums
Satellites
https://platform.leolabs.space/visualizations/leo
Modulation
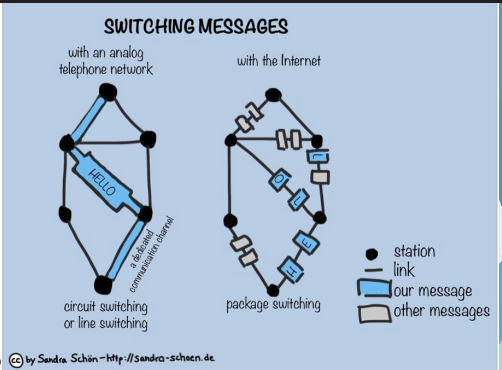
Switching messages
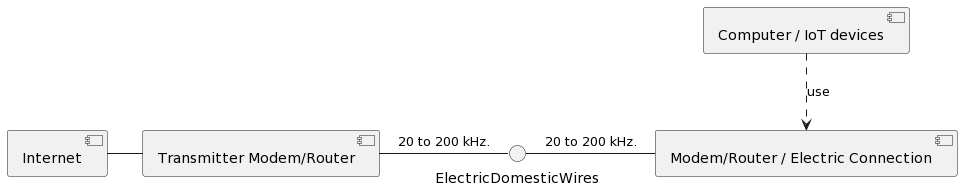
What is Power Line Communications (PLC)?
PLC means Power Line Communications and it stands to transmit voice and data by the existent electric network. This system could communicate to 200 Mbps.
United Utilities and Northern Telecom purposed Internet was available by the electric network; it’s called Power Line Communications.
PLC devices work as follows: a wave is digitally modulated between 20 to 200 kHz that is injected into electric domestic wires where each receptor has a unique address and it’s managed individually by a signal transmitter.
Worked examples
Data Link Layer
Ethernet
| Tamano | ||
| Preambulo | 8 bytes | |
| MAC destino | ||
| MAC fuente | ||
LLC. Logical Link Control. It is a software that communicates .
MAC. It is a hardware. Network device.
48 bits.
OUI. 3 octetos identifies providers.
UAA.
Hexadecimal.
Entre mas grande quieras el mensaje, más pesado es revisarlo.
ATM → Frame Relay → Ethernet
ARP
Error detection
Bit Error Rate
Packet error ratio
BER device
Detector
Corrector
Bit de paridad. Redudant.
Checksum
Cyclic redundancy check
CRC
Forward Error Correction
https://emn178.github.io/online-tools/crc32.html
https://emn178.github.io/online-tools/
Hamming.
Convutionals.
RS (Reed Solomon)
LDPC (Low Density Parity Check) o Gallager
Network Layer
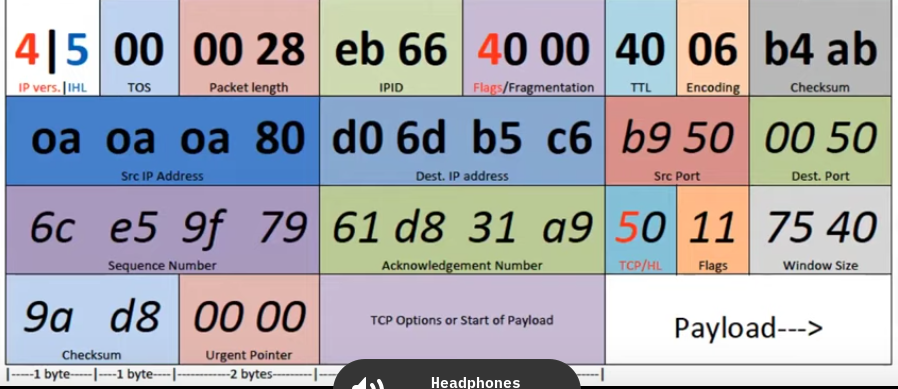
1969
Darpanet. Academic and . Darpa.
IPv4 and IPv6
Internet2
IPv4 Classes
MIC.mx, AKKY
ICAAN, Registers
WhoIS
MAC
Subnet mask
Gateway. Access points.
Private.
Public.
ReservedDARPADARPA.
DHCP. Dynamic
DNS
Internet Society
worldipv6launch.org
Hop (networking)
NSFnet.
Advanced Research Projects Agency
TCP/IP
Enterprises & Tim Bernee-Lee.
Tec de Monterrey.
https://www.worldiv6launch.org
https://pulse.internetsociety.org/
Private network and public network
NAT
https://www.practicalnetworking.net/
https://www.practicalnetworking.net/series/nat/nat/
WLAN Wireless. WPAN, WLAN, WMAN, WWAN.
| Definicion | Ejemplo | |
| WPAN | ≤10 metros | ZigBee, Bluetooth |
| WLAN | IEEE 802.11, ETSI | Wifi, HiperLAN |
| WMAN | 3G,4G,5,G |
WiFI versions
OFDM
OFDMA
MU-MIMO
Radio
FHSS (Frequency Hoping)
DSSS
Topologias
Ad Hoc
Peer
Master Slave
Infraestructura
Access point
WMAN
Wireless Bridge (WB)
Network address translation
Network Address Translation (NAT) is a process carried out by a network device, often a router or a firewall, that maps a source and destination IP address from one network address space (typically a private network) to another (typically a public network like the Internet). To accomplish this, the NAT device, usually located at the network edge, modifies the headers of the source and destination packets in a manner that is transparent to the end nodes. This process may involve any ports in the networks, a variant of which is referred to as Port Address Translation (PAT), NAT Overload or Port forwarding. PAT allows multiple devices on a private network to share a single public IP address or a few public IP addresses by differentiating each device based on the unique source port of its outgoing packets.
NAT could perform different kind of mapping. Some of those are:
- Static NAT: A one-to-one mapping between addresses.
- Dynamic NAT:
- Static PAT:
- Dynamic PAT:
NAT Traversal
How can you have noted NAT gateway provide a one or a few single public IP addresses, but it has a big problem, how can you build P2P applications or end-to-end protocols if incoming connection requires some configuration and your users don’t want configure its routers to set a stable public IP? The solution is implement somehow a NAT traversal.
Some of the solutions the people have invented are:
The Circuit Relay approach that consists in a STUN, TURN, and ICE.
UDP/TCP hole punching.
UPnP (Universal Plug and Play) and NAT-PMP (NAT Port Mapping Protocol)
Network Utilities
PING
https://www.youtube.com/watch?v=IIicPE38O-s&ab_channel=PowerCertAnimatedVideos
Traceroute
. (2022, October 04). Traceroute (tracert) Explained - Network Troubleshooting. Youtube. Retrieved from https://www.youtube.com/watch?v=up3bcBLZS74&ab_channel=PowerCertAnimatedVideos
Open Visual Traceroute. (2022, May 14). Retrieved from https://visualtraceroute.net
IP
https://pages.di.unipi.it/ricci/501302.pdf
https://gist.github.com/sanchezcarlosjr/8ceadc87deeaa49e4678622a102c2448
Network typologies
- Physical. It means the layout of nodes and cables. It is a particular concern of the physical layer (1) of the OSI model.
- Logic. It means the way that the signals act on the network media. A particular concern of the network layer (3) of the OSI model.
A topology can be implemented in different logical and physical ways. We’ll focus on the logical way.
Data networks hardware
classDiagram
class Network {
Map~Link, Node1, Node2~
Set~Node~
}
Network o-- Link
Network o-- Node
Link <|-- WiredTechnology
Link <|-- WirelessTechnology
WiredTechnology <|-- CoaxialCable
WiredTechnology <|-- Ethernet
WiredTechnology <|-- OpticalFiber
Node <|-- NetworkInterface
Node <|-- Repeater
Node <|-- Hub
Node <|-- Bridge
Node <|-- Switch
Node <|-- Modem
Node <|-- Firewall
class NetworkInterface {
end device
}Connecting two routers
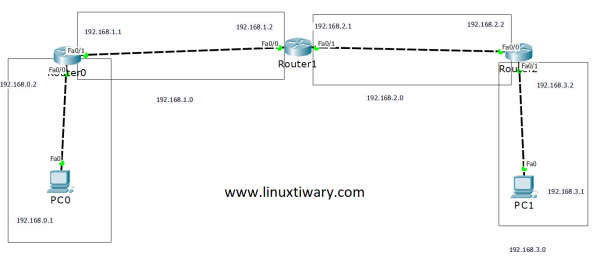
RIP Routing Configuration using Three Routers in Cisco Packet Tracer. (2020, April 30). Retrieved from https://linuxtiwary.com/2020/04/29/rip-routing-configuration-using-three-routers-in-cisco-packet-tracer
Network modeling
CISCO Packet Tracer
GNS3
Classless Inter-Domain Routing
Wireless
Factores.
Tipo e red.
Proprogracion.
Material.
Consideraciones ambientales.
Otras senanales.
Energia. Conexiones. (PoE) PowerOverEthernet IEEE 802.3af
WLAN a una red cableada.
Cobertura.
Seguridad.
USA prohibicion de WLAN.
SSID (Service Set Identifier)
Seguridad informatica.
Asociaciacion maliciosa.
Attack in Middle.
Mac Spooffing. Kismet, Ethereal.
Wardriving. (Escaneo de redes).
DD-WRT, Open WRT, Tomato (Firmware para routers), OpenVPN.
Políticas de seguridad.
Protocoloes de autenticación para WIFI. EAP, LDAP, Kerberos, OAuth2, SAML2, Radius, TACACS+, FreeRadius, etc. (Cuando entras a una red y te parece una autenticacion personalizada esto sería).
WPA, WPA2, WPA3 (CowPatty, Cain, Abel).
VPN tunneling.
IPSec, SSL, PPTP
Smart Cards, SIM Card.
Logical network topology classification
Point-to-point
Bus
General Model

A possible CISCO Packet Tracer Implementation
Download the Packet Tracer File
Star
General Model
A possible CISCO Packet Tracer Implementation
Download the Packet Tracer File
Ring
General Model
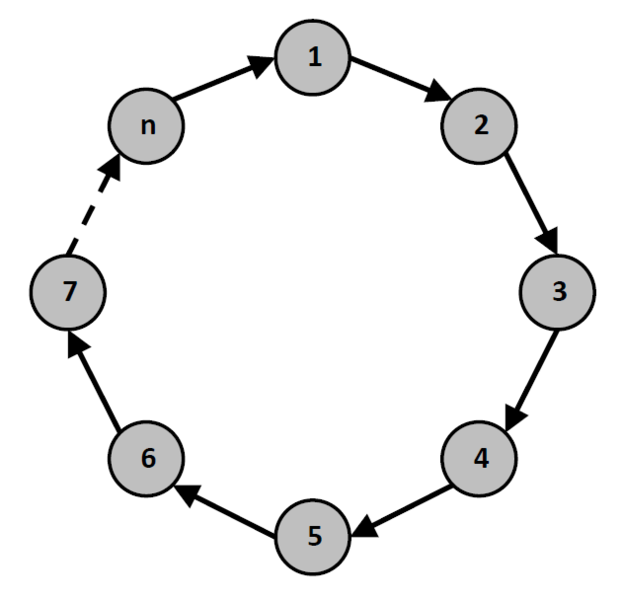
A possible CISCO Packet Tracer Implementation
Download the Packet Tracer File
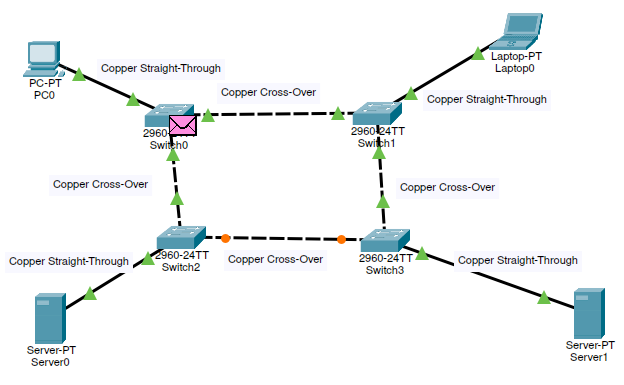
Mesh
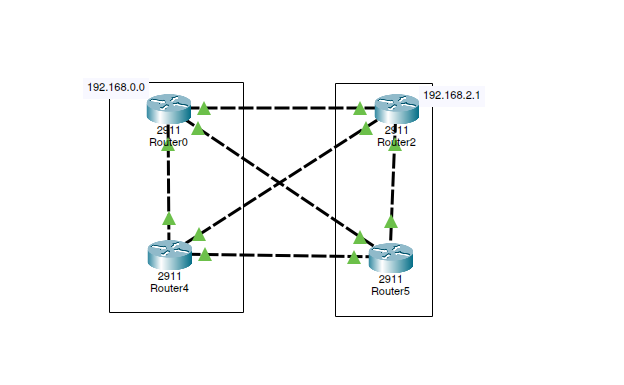
Download the Packet Tracer File
Tree
A possible CISCO Packet Tracer Implementation
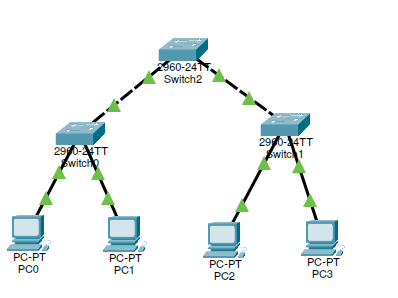
Download the Packet Tracer File
Mix
A possible CISCO Packet Tracer Implementation
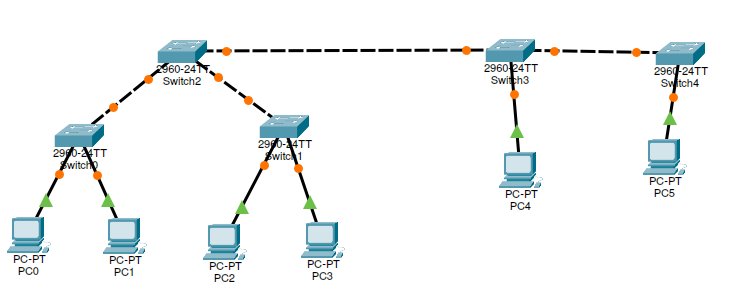
Download the Packet Tracer File
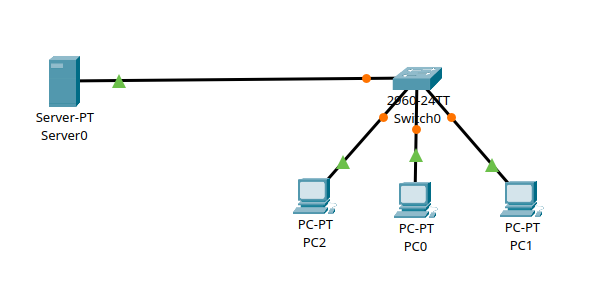
DCHP
DCHP from server
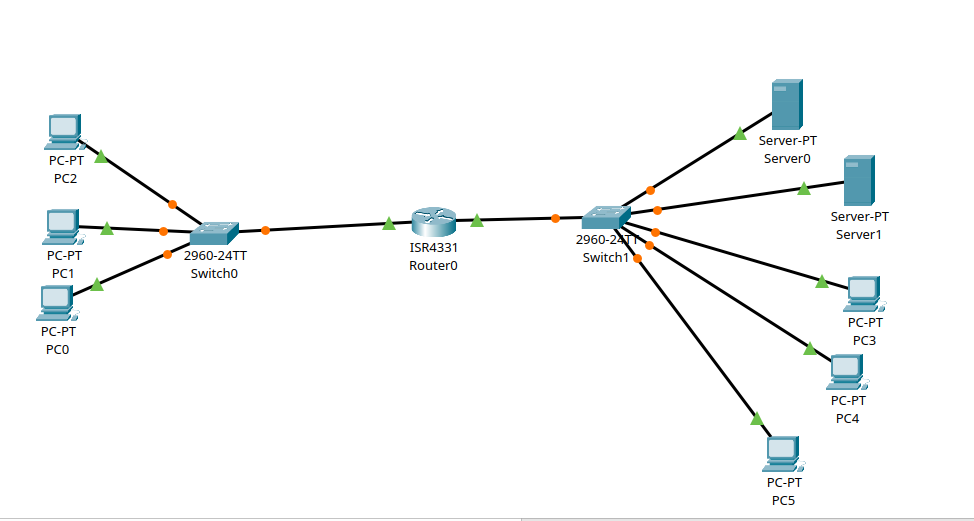
DCHP from server to two networks
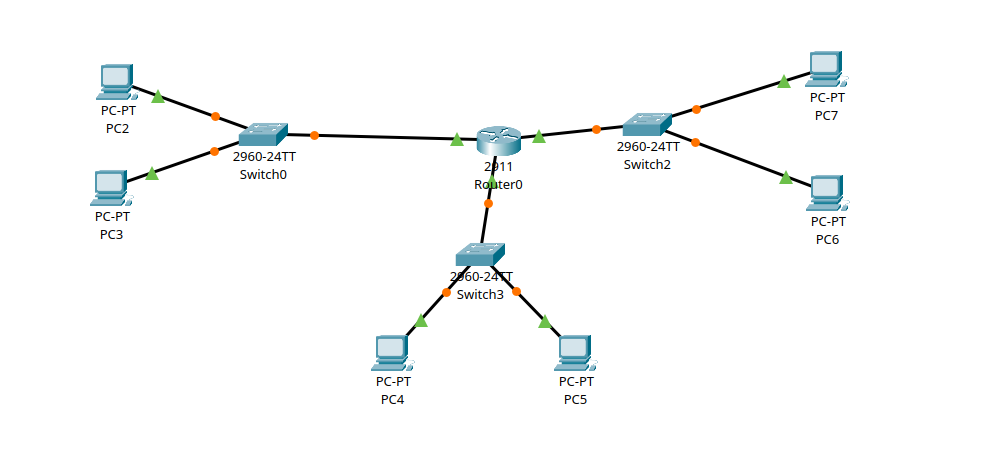
DCHP from routers
We don’t have to assign an IP manually, we can use DCHP from servers or routers.
Address Resolution Protocol (ARP) and Reverse Address Resolution Protocol (RARP)
Address resolution protocol is a network protocol in OSI layer 2.5 for discovering the link-layer address, such as MAC Address.
If you have IP and you don’t have MAC Address, then you need ARP.
If you don’t have IP and you have MAC Address, then you need RARP.
| MAC Address | IP |
| 5F-AF-AB-36-52-38 | |
| BA-81-42-0E-80-93 | |
| B0-78-91-5E-DD-0A |
ARP Table.
Froehlich, A. (2021). Reverse Address Resolution Protocol (RARP). SearchNetworking. Retrieved from https://www.techtarget.com/searchnetworking/definition/Reverse-Address-Resolution-Protocol
Networking Relationship
Which resources can be shared? files, directories, software, disks, …
Client/Server
Peer-to-peer P2P
CSMA/CD
carriers telecom
VLAN
Clara, G. L. (2014, May 24). CURSO 9-1 Explicacion de Tecnologia VLAN. Youtube. Retrieved from https://www.youtube.com/watch?v=PBMQVjSxCQU&ab_channel=gustavoLobatoclara
Worked examples
FAQ
References
3. Larry L. Peterson and Bruce S. Davie. Computer Networks: A Systems Approach, Morgan
Kaufmann Publishers, 5th edition, 2011.
4. William Stallings. Data and Computer Communications, Prentice Hall, 9th edition, 2010.
5. Uyless D. Black. Computer Networks: Protocols, Standards, and Interfaces, Prentice Hall,
2nd edition, 1993.
6. Fred Halsall. Data Communications, Computer Networks and Open Systems, Addison-
Wesley, 5th edition, 2005.
7. Douglas E. Comer. Computer Networks and Internets, Prentice-Hall, 5th edition, 2009.
Bibliografía complementaria:
1. Uyless D. Black. IP Routing Protocols: RIP, OSPF, BGP, PNNI and Cisco Routing
Protocols, Prentice-Hall, 2000.
2. Gerard J. Holzmann. Design and Validation of Computer Protocols, Prentice-Hall, 1991.
3 Uyless D. Black. Computer Networks: Protocols, Standards, and Interfaces, Prentice Hall,
2nd edition, 1993
Transport Layer
UDP
UDP makes sense for these types of applications:
- It has small requests and responses. For instance, DNS, NTP, SNMP, DCHP, Syslog
- It has built-in delivery confirmation system because if you does the communication over TCP TCP and you application are end up working against each other. For instance, TFTP, RTP, SNMP, QUIC.
- It involves live or streamed content because the latest/real time packet is more important than older dropped packet. For instance, VoIP, RTP, SRTP, SIP, H.323, LiveTV, Multiplayer Video Games.
TCP
QUIC
Ethernet.
F
https://hpbn.co/building-blocks-of-tcp/
https://www.iana.org/assignments/service-names-port-numbers/service-names-port-numbers.xhtml
Session Layer
Network Time Protocol
DNS, LDAP
NetBIOS/IP
RPC
PPT
SSH
Sockets API
IPsec
Worked example
Write the UDP frame to establish a TCP connection for an HTTP request.
FAQ
It is possible to establish UDP datagrams over a TCP stream?
Yes, check out mullvad. (2022, October 13). udp-over-tcp. Retrieved from https://github.com/mullvad/udp-over-tcp
Presentation Layer
Compression, Encryption, and Format.
ASCII, Unicode, LPP, NCP, X.25 PAD, SSL, IPsex, DES, PGP.
Protocols.
Base64
Application Layer
Protocols
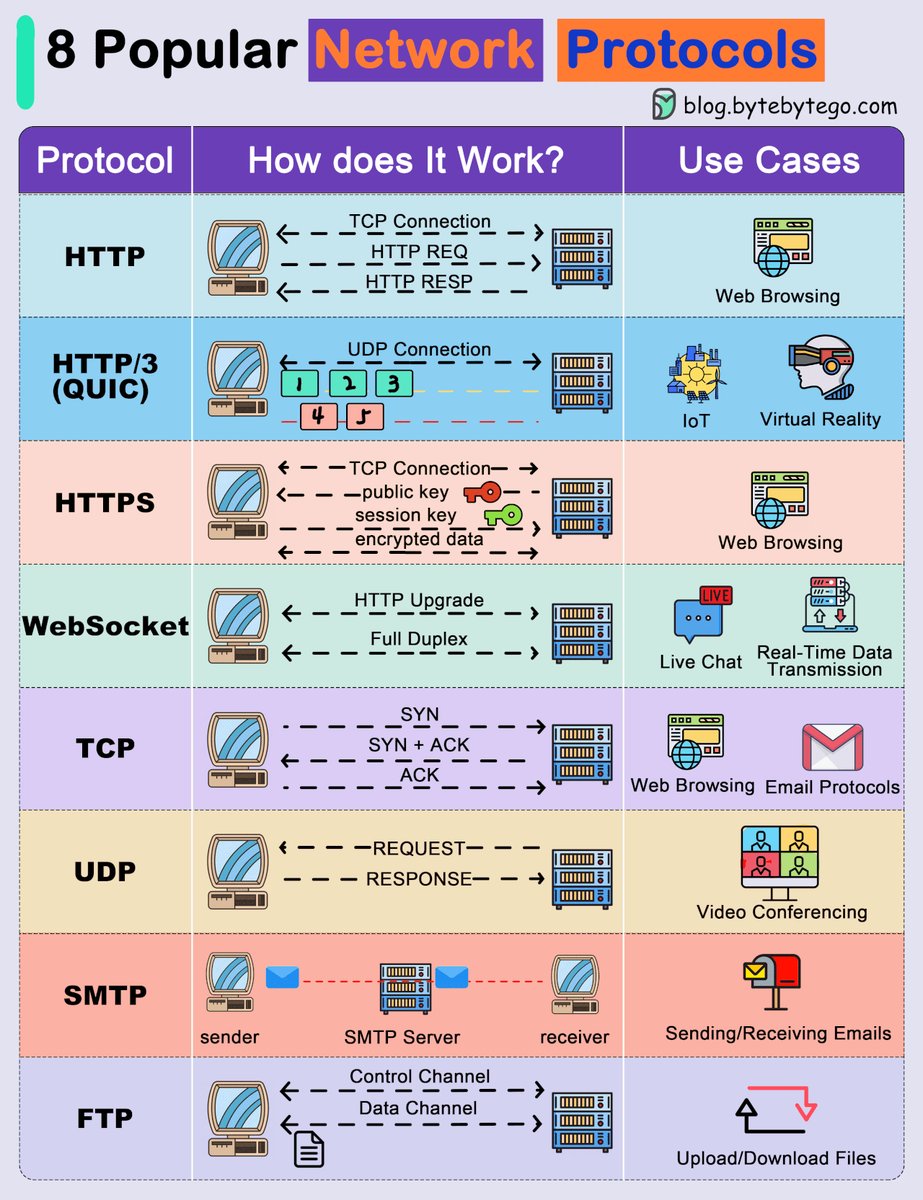
Protocols are procedures for communication whereas standards are well-known procedures.
You can make your own protocols, but they necessarily don’t mean a standard protocol.
FrippeMax. (2011, January 03). Warriors of the Net HD. Youtube. Retrieved from https://www.youtube.com/watch?v=PBWhzz_Gn10&ab_channel=FrippeMax
Wang, O. (2022). What are Standards? Why are They Important? - IEEE SA. IEEE Standards Association. Retrieved from https://standards.ieee.org/beyond-standards/what-are-standards-why-are-they-important
What's the difference between the terms "protocol" and "standard"? (2022, November 08). Retrieved from https://softwareengineering.stackexchange.com/questions/105449/whats-the-difference-between-the-terms-protocol-and-standard
Application Architecture
- P2P (Peer to Peer)
- Client to Server
Asynchronous communication
HTTP/Web
Fielding, R., Gettys, J., Mogul, J., Frystyk, H., Masinter, L., Leach, P., & Berners-Lee, T. (1999, June). Hypertext Transfer Protocol -- HTTP/1.1. doi: 10.17487/RFC2616
JSON Web Token
Common Gateway Interface
HTML
XML
Web 1.0
Web 2.0
Web 3.0
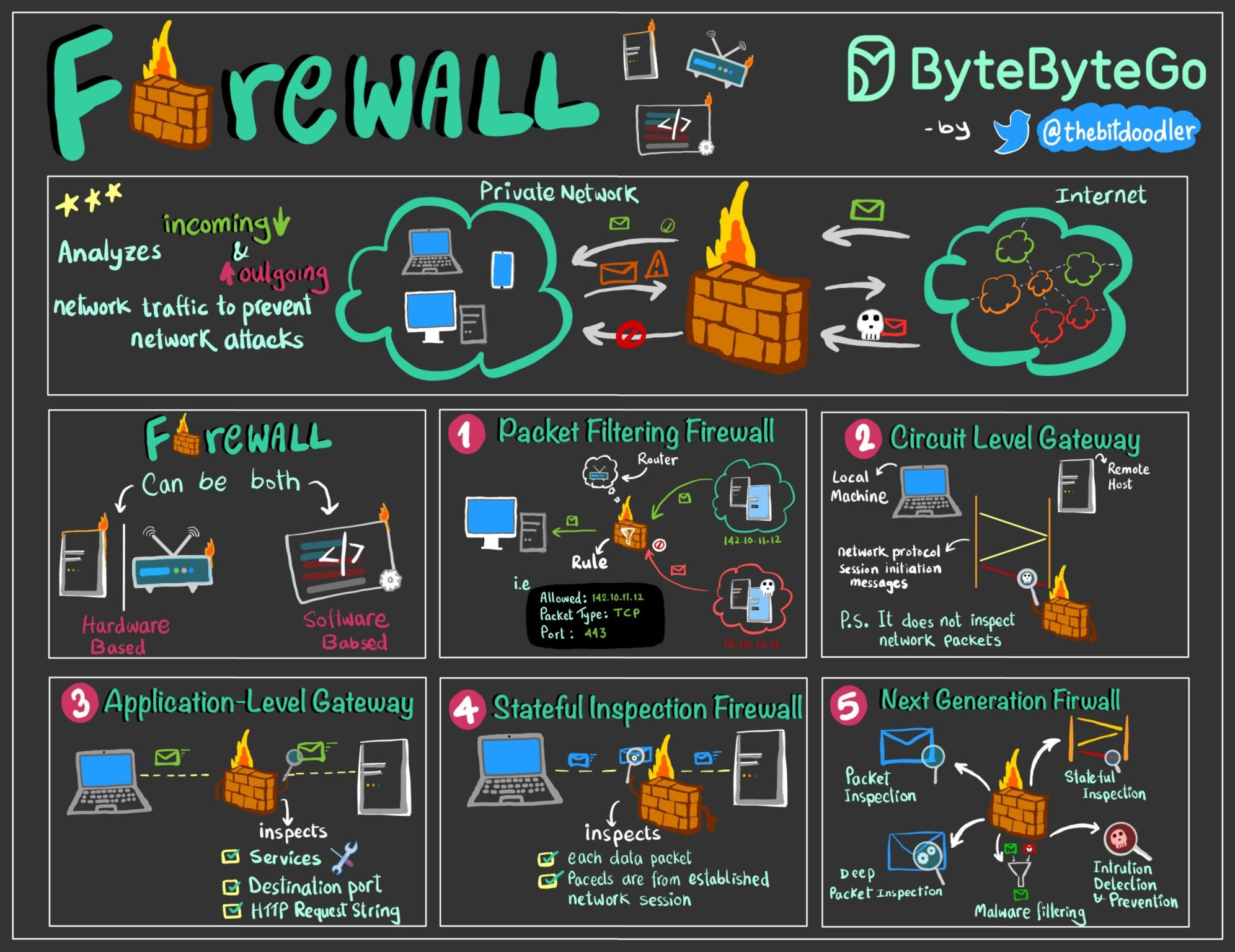
Firewall
SSL
Telnet
DHCP
SMTP
X Windows
FTP
DNS
TTL
In DNS, is a lower TTL better?
Records
A
AAAA
ipv6 and ipv4 choice
Network layer
Browser
Library
WebRTC
WebSockets
WebTransport
SSH
Reverse tunneling with SSH, docker and ngnix (A open source alternative to ngrok and cloudflare)
ssh -nN -f -R 0.0.0.0:remote-port:localhost:local-port username@remote-ipMake sure sshd_config has the property GatewayPorts equals to yes.
In the remote server, use ngnix, we’re going to use Nginx Proxy Manager container because it easier to set up correctly.
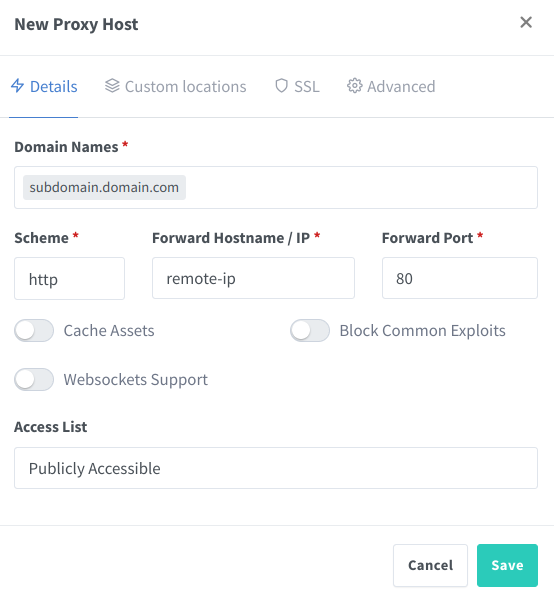
How to Run Graphical X Apps and Wayland apps Over SSH in Linux
ssh -X remote-user@remote-hosthttps://gitlab.freedesktop.org/mstoeckl/waypipe
waypipe ssh user@theserver weston-terminalGoing through one host to reach another server
https://askubuntu.com/questions/311447/how-do-i-ssh-to-machine-a-via-b-in-one-command
https://unix.stackexchange.com/questions/25055/ssh-via-multiple-hosts
https://www.cyberciti.biz/faq/linux-unix-ssh-proxycommand-passing-through-one-host-gateway-server/
VPN
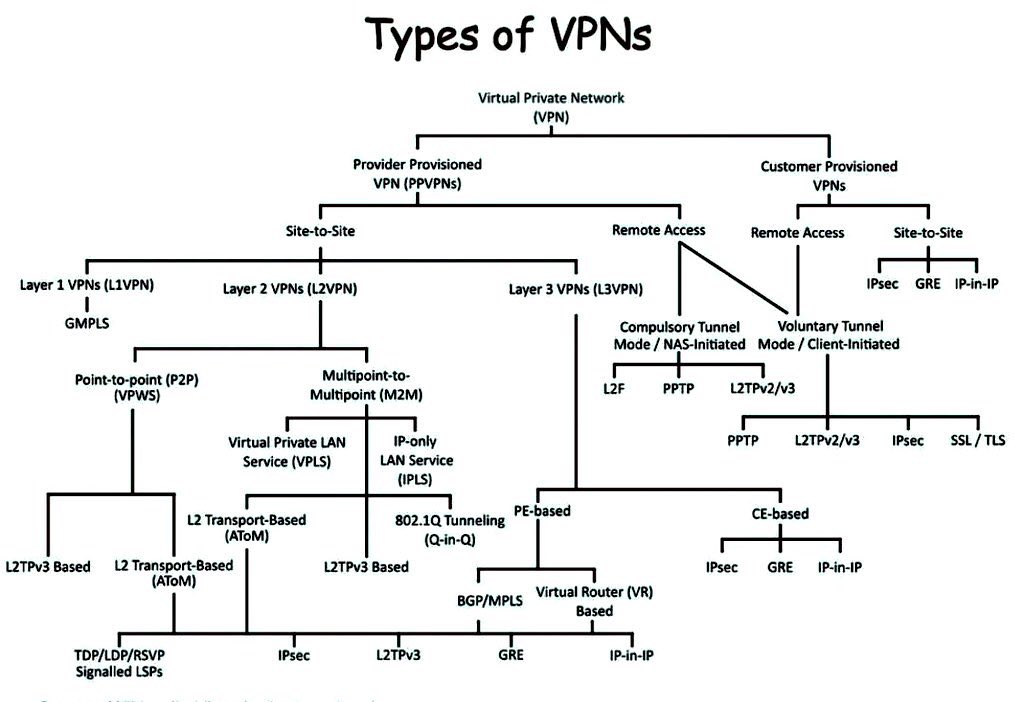
Security.
Learn - VPN University. (2021, November 19). Retrieved from https://www.vpnuniversity.com/learn
OpenVPN
Virtual Private Network (VPN) | An Introduction - GeeksforGeeks. (2022, September 29). Retrieved from https://www.geeksforgeeks.org/virtual-private-network-vpn-introduction
WireGuard — fast, modern, secure kernel VPN tunnel
Virtual Private Networks, Second Edition O'Reilly
Mastering OpenVPN: 9781783553136
OpenVPN - ArchWiki. (2022, October 11). Retrieved from https://wiki.archlinux.org/title/OpenVPN
VNC. Virtual Network Computing
, RDP, RFB, NX
Virtual Network Computing A Complete Guide by Gerardus Blokdyk
Web+VNC references
Apache Guacamole™. (2022, September 13). Retrieved from https://guacamole.apache.org
noVNC. (2021, November 11). Retrieved from https://novnc.com/info.html
Johnson, K. (2022). Browser VNC with Zero Trust Rules. Cloudflare Blog. Retrieved from https://blog.cloudflare.com/browser-vnc-with-zero-trust-rules
Kaplinsky, C. (2022, October 12). TightVNC Java Viewer Version 2. Retrieved from https://www.tightvnc.com/release-jviewer2.php
Render a VNC client in browser · Cloudflare Zero Trust docs. (2022, October 12). Retrieved from https://developers.cloudflare.com/cloudflare-one/tutorials/vnc-client-in-browser
VNC on the Internet.
Johnson, K. (2022). Browser VNC with Zero Trust Rules. Cloudflare Blog. Retrieved from https://blog.cloudflare.com/browser-vnc-with-zero-trust-rules
VNC
Becoming GUI Applications to Web apps with VNC
C.6. Accessing Graphical Applications Remotely Red Hat Enterprise Linux 6 | Red Hat Customer Portal. (2022, October 13). Retrieved from https://access.redhat.com/documentation/en-us/red_hat_enterprise_linux/6/html/deployment_guide/s1-x-accessing_graphical_applications_remotely
https://blog.cocalc.com/cocalc/2018/11/05/x11.html
Sometimes we have an application build a desktop GUI application such as Tkinter, …
https://github.com/Xpra-org/xpra/
Gaskin, P. (2020). How To Remotely Access GUI Applications Using Docker and Caddy on Debian 9. DigitalOcean. Retrieved from https://www.digitalocean.com/community/tutorials/how-to-remotely-access-gui-applications-using-docker-and-caddy-on-debian-9
https://github.com/nicedexter/docker-gui
CloudTk Home Page. (2022, October 13). Retrieved from http://cloudtk.tcl-lang.org

RDP (Remote Desktop Protocol)
https://superuser.com/questions/32495/whats-the-difference-between-rdp-vs-vnc
https://github.com/Genymobile/scrcpy
Internet Relay Chat (IRC)
Telnet
Tunneling
For my money the best out-of-box tunneling service is Cloudflare.
anderspitman. (2022, September 25). awesome-tunneling. Retrieved from https://github.com/anderspitman/awesome-tunneling
https://en.wikipedia.org/wiki/Tunneling_protocol
Torrent
Tor
Distributed systems. Concurrent systems.
Celery - Distributed Task Queue — Celery 5.2.7 documentation. (2022, May 29). Retrieved from https://docs.celeryq.dev/en/stable/index.html
Consensus and agreement algorithms
Kshemkalyani, A. D., & Singhal, M. (2008). Consensus and agreement algorithms. Distributed Computing: Principles, Algorithms, and Systems. Cambridge University Press. doi: 10.1017/CBO9780511805318.015
Docker
Docker, Vagrant, VMs, Cloud, OpenStack
Kubernetes
Microservices
donnemartin. (2022, November 03). system-design-primer. Retrieved from https://github.com/donnemartin/system-design-primer
Architectural design
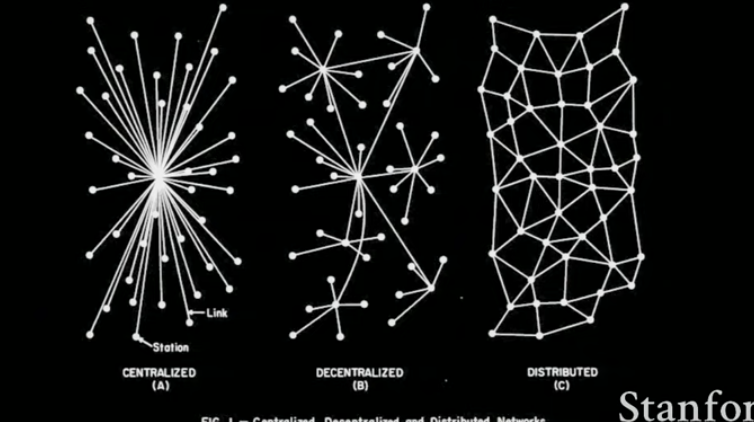
CS556 - Distributed Systems. (2012, June 14). Retrieved from https://www.csd.uoc.gr/~hy556/material.html
- Client-server (2-tier, 3-tier, ntier, cloud computing exhibit this style)
- Peer-to-peer (P2P)
Decentralized model.
Stanford Online. (2015, October 22). Stanford Seminar - IPFS and the Permanent Web. Youtube. Retrieved from https://www.youtube.com/watch?v=HUVmypx9HGI&ab_channel=StanfordOnline
yggdrasil/cjdns/hyperbora
MIT Digital Currency Initiative. (2022, September 25). Retrieved from https://dci.mit.edu/decentralizedweb
Peer to peer | Everything I know. (2022, September 25). Retrieved from https://wiki.nikiv.dev/networking/peer-to-peer/#links
Beaker | A peer-to-peer browser for Web hackers. (2022, September 25). Retrieved from https://beakerbrowser.com
Blockchain
Jami
JXTA
IPFS powers the Distributed Web
https://developers.cloudflare.com/web3/
Blockchain
Proof-of-state
Polkadot, Layer 1, Layer 2, relay chain
parachain
Bridges, XM
WASM, WebAssembly
Decentralized autonomous organizations (DAOs)
dApps
Smart contracts
Kusama
https://wiki.gear-tech.io/docs/getting-started-in-5-minutes/
POW
Old blockchain
Specify languages
VM
Proof of stake, proof of work
microservice = smart contract
DeFi, DEX, NFT, social tokens
Substrate
Actor model
Gear Toolkit. WebAssembly Virtual Machine. EVM (Solidity), BPF (Solana) y WASM VM.
GAS
DNS Polkadot
PolkadotName System
Centralized mode. Cloud
Jobs. Site Reliability Engineering, System Administration, and DevOps
SRE https://sre.google/sre-book/table-of-contents/
System Administrators
Ubiquitous computing. Pervasive computing.
The Internet of Things (IoT) is a subclass of Ubiquitous Computing.
What's the difference between IoT and pervasive (ubiquitous) computing? (2020, August 21). Retrieved from https://www.researchgate.net/post/Whats-the-difference-between-IoT-and-pervasive-ubiquitous-computing
Security
Appendix
Decibels
dB ↔ dBWatts
dBmW ⇒ millwats.
The measure is the logarithm. 1
History. Bell.
Definition. “Decibels” is a logarithm relative measurement to watts.
Relative to watts.
Behavior.
Amplifier. Dimmer.
Gain.
fromWattsToDecibels :: Float -> Float
fromWattsToDecibels x = 10*log10(x)
fromDecibelsToWatts :: Float -> Float
fromDecibelsToWatts x = 10^(x/10)
fromDecibelsToWatts :: Float -> Float
fromDecibelsToWatts x = 10^(x/10)No negative decibels.
Multimedia
Conversion between formats.
Bitrate to
Telecommunication limits
Bandwidth signal.
Noise. Attenuation. Reflection. Diffraction.
Politics.
Market
Telecommunication statistics
Mexico
- Televisa
- Telmex
TODO
Zero-knowledge architecture.
roaming
APN
https://www.xatakamovil.com/conectividad/que-es-eso-del-apn-y-para-que-sirve